KMIP Keymaster Middleware¶
Overview¶
KMIP Key Master is for data at rest encryption for Swift, using a KMIP compliant external key management service
Note
If you are currently using Keymaster Middleware you will not be able use KMIP Keymaster. If you want to convert to KMIP Keymaster please contact support. You can only have one Keymaster Middleware configured at a time.
KMIP Keymaster middleware should be deployed in conjunction with the Encryption Middleware.
Implements key management for the Encryption Configuration feature.
Limitations¶
This middleware can not be disabled once it has been deployed. It is required to provide keys for previously written encrypted data.
Note
Currently, you may only enable the KMIP Keymaster middleware before the initial deployment of the cluster. If you are interested in using encryption on an existing SwiftStack cluster, please contact support.
Settings¶
Be sure the Enabled box is checked.
host - A string representing either a hostname in Internet domain notation
or an IPv4 address
port - An integer representing a port number. Recommended to be 5696 according
to the KMIP specification
username - A string representing the username to use for KMIP requests.
Optional depending on server access policies. Leave blank if not needed.
password - A string representing the password to use for KMIP requests.
Optional depending on server access policies. Leave blank if not needed.
certfile - A string representing a path to a PEM-encoded client certificate file.
keyfile - A string representing a path to a PEM-encoded client certificate key file.
The private key contained in the file must correspond to the certificate pointed to by certfile.
ca_certs - A string representing a path to a PEM-encoded certificate authority certificate file.
This certificate will be used to verify the server’s certificate when establishing a TLS connection.
Staged Key Name - This is an internal SwiftStack name. Use this to provide an identifying
name for the key. May only include lower-case letters, numbers, dashes, or underscores.
Staged KMIP ID - The unique identifier for the AES-256 secret key that will be retrieved from the KMIP service.
Generating and Installing Certificates¶
Generating SSL certificates for the cluster can be completed by using the controller to generate a Certificate Signing Request (CSR). The following procedure will create your certfile, keyfile and sign the certificate with your KMS CA store. You will also need to export the CA Cert from your KMS to be used for the ca_certs file.
Generate a Private Key and a Certificate Signing Request (CSR)¶
Log into your SwiftStack controller and run the following commands:
- Generate the Private Key file
openssl genrsa -out /var/tmp/kmip.keyfile 4096openssl genrsa -out /var/tmp/kmip.keyfile 4096 Generating RSA private key, 4096 bit long modulus ..................++ .................................++ e is 65537 (0x10001)
- Generate the CSR
openssl req -new -key /var/tmp/kmip.keyfile -out /var/tmp/kmipcert.crsopenssl req -new -key /var/tmp/kmip.keyfile -out /var/tmp/kmipcert.crs You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:US State or Province Name (full name) []:California Locality Name (eg, city) [Default City]:San Francisco Organization Name (eg, company) [Default Company Ltd]:SwiftStack Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:kmipclient.swiftstack.tech Email Address []:support@swiftstack.com
- Sign the certificate with your Certificate Authority (CA)
The following example uses an external KMS such as SafenetAT Keysecure
- On the KeySecure Management Console, click the Security tab.
- Click the Local CAs option in the left menu.
- Click the radio button of the CA that is to sign the certificate request, and click the Sign Request button under it.
- Select Client as the Certificate Purpose and set the desired Certificate Duration period per security policy.
- Paste the certificate request data still in your buffer into the Certificate Request field.
- Click the Sign Request button.
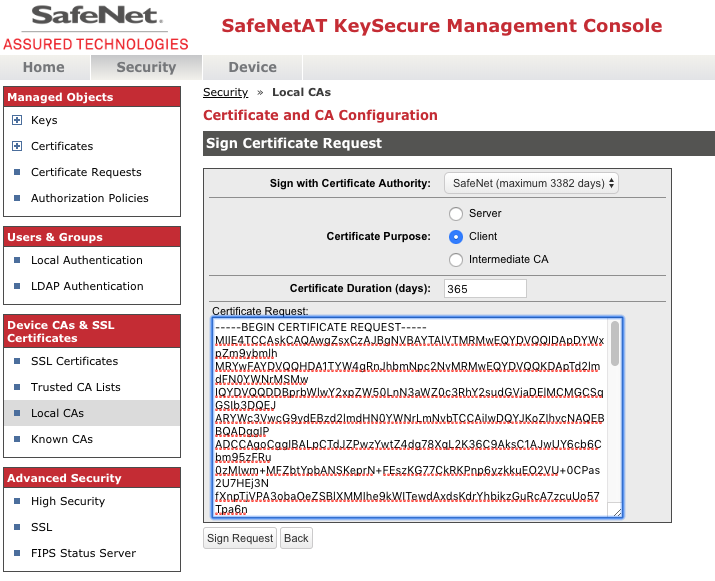
- Click the Download button to download the signed client certificate. Save this file as certfile.crt
- Click the Back button to return to the Local CAs page.
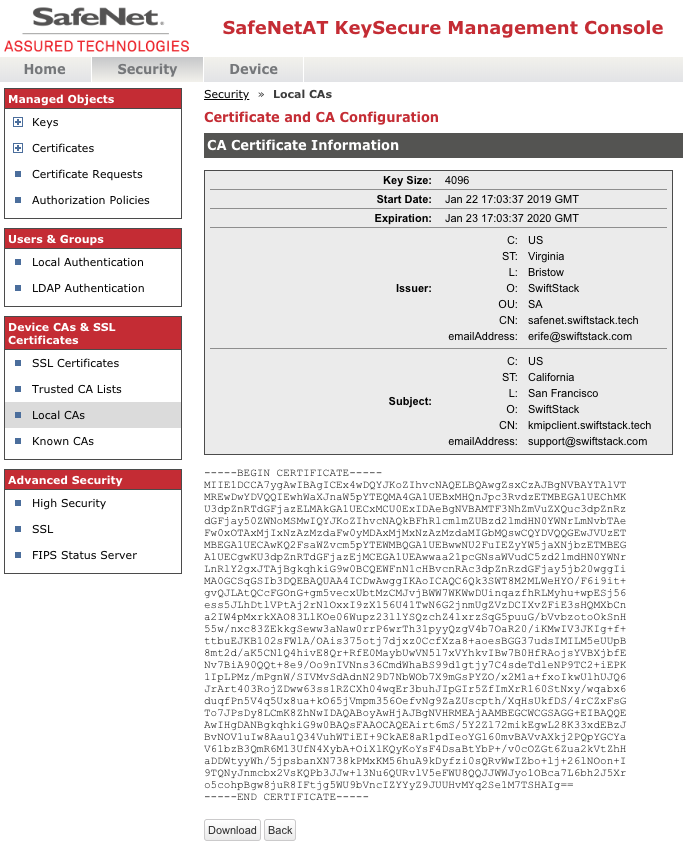
- On the Local CAs page click the Download button. Save this file as ca_certs.crt
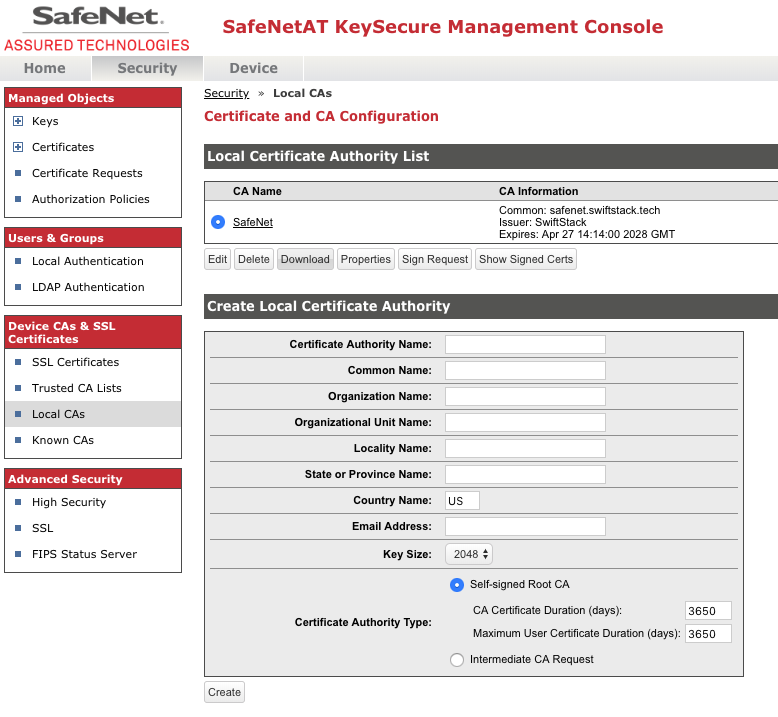
You should now have the two certificates and the key file that are needed to enable KMIP Keymaster within the SwiftStack Middleware. Getting the CSR signed can be performed by any CA that your external KMS solution recognizes.